In modern Software Development practices, use of containerisation is increasing significantly within a DevOps culture. Most of these environments benefit from the rich features provided by containerisation such as scalability, portability, and process isolation.
However, it is important to think of “how secure” a software really is before we ship it to our clients. While creating container images as our releases, heavy use of third party and outdated libraries can introduce added vulnerabilities to the images we ship. Therefore, a solid way of scanning container images is needed. A few solutions are currently available in the market, but the most commonly used open source image scanning tool is CoreOS Clair.
Clair is an open source vulnerability scanning platform by CoreOS and it provides static analysis of Docker Container Images. It can directly integrate with CoreOS (Red Hat) quay.io, Quay Enterprise, Dockyard, and many other registries.
How Clair Works
Clair consists of 3 main components:
1. API server
2. PostgreSQL database
3. CVE Data Sources
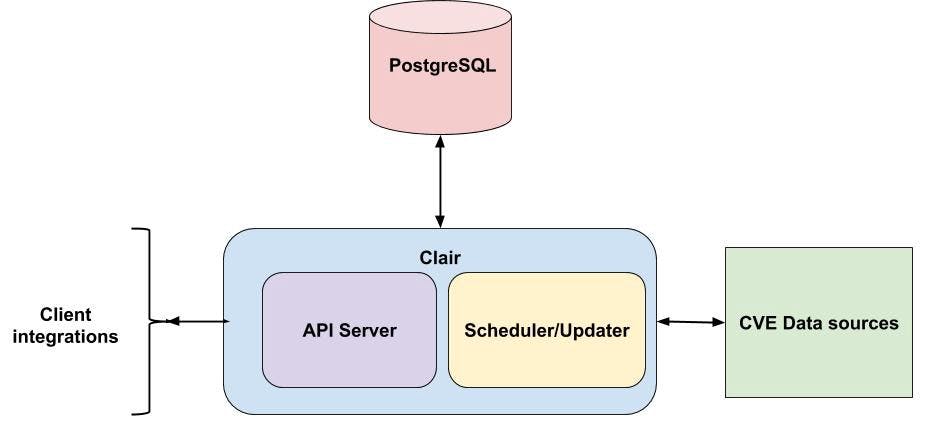
Clair does not have a CLI or a UI to interact with — the API server provides a REST API interface to interact with Clair. There are many CVE (Common Vulnerability and Exposure) sources Clair works with, such as Debian Security Bug Tracker, Ubuntu CVE Tracker, and NIST NVD.
Built-in drivers:
Debian Security Bug Tracker
Ubuntu CVE Tracker
Red Hat Security Data
Oracle Linux Security Data
Amazon Linux Security Advisories
SUSE OVAL Descriptions
SUSE OVAL Descriptions
Alpine SecDB
NIST NVD
CVE updater is in sync with these sources and updates vulnerability database. The API interface is used to interact with Clair to scan images and layers before updating the database.
Clair does static scanning which means it scans the image and not the running container instance of it. Docker images consist of one or more layers, which are also images and stored in docker registry as blobs. So, Clair, analyses these layers or a collection of multiple layers (an image).
Deployment Patterns
Clair can be deployed in different ways but the most commonly used methods are Docker Compose and Kubernetes-based deployments:
1. Deploy in Kubernetes — Could be easily deployed in Kubernetes with Clair Helm Chart (with the version 3.0.0-pre which is a pre release as of now) or deploy it with the yaml files provided with the 2.0 release.
2. Using Docker Compose — A few commands to run Clair in the Docker runtime.
Clair Client Integrations
Since Clair provides REST API only, there are client integration tools to interact with Clair. And most of them helps us to integrate static image scanning to our build and delivery pipelines.
Klar
Klar is a command line tool which can be used to analyse docker images stored in a private or public docker registry and even with ECR or GCR. It is also a single binary file without any dependencies. Klar runs with a set of environment variables as configurations and when it runs, it works between Clair API server and the registry.
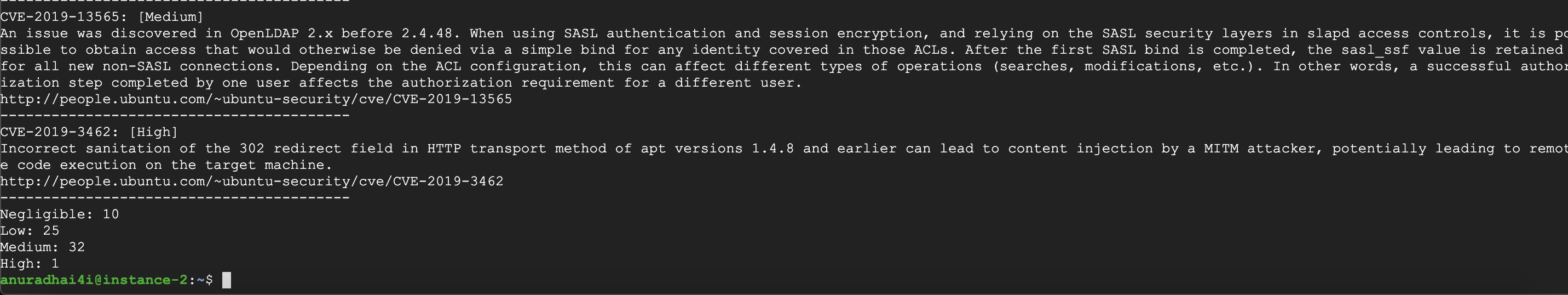
The scan output can be captured to a text file or a JSON file, and can be used to list and provide additional information for the captured vulnerabilities.
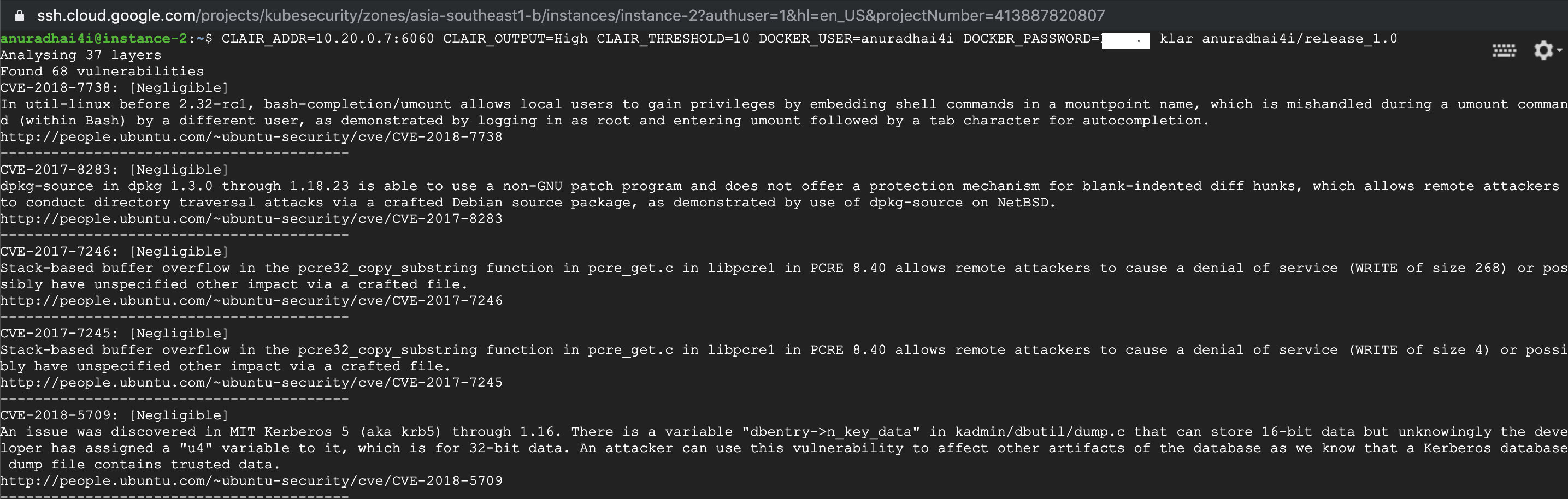
End of the output:
Clairctl
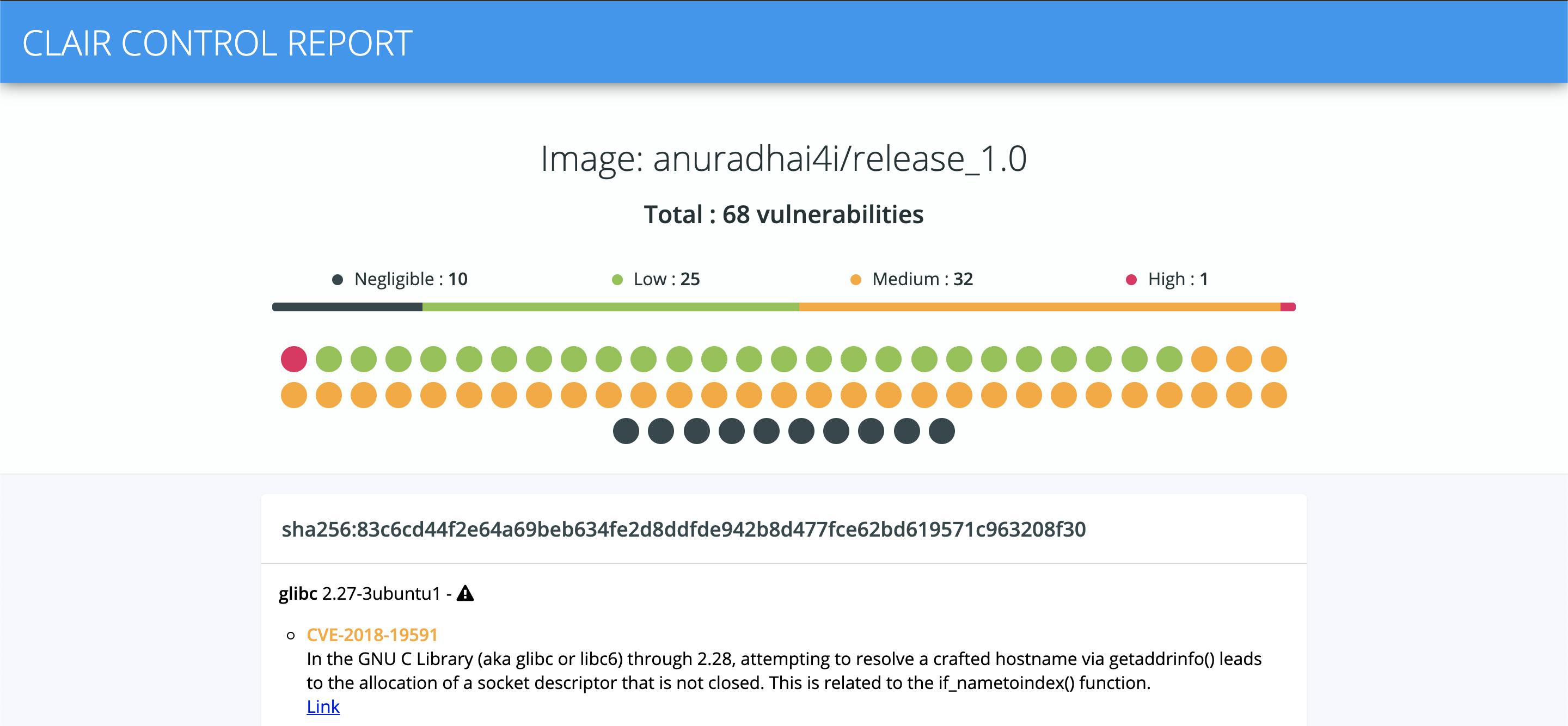
Clairctl is also lightweight command line tool that works between the Clair AIP server and registries. Most importantly, Clairctl functions as a reverse proxy for authentication. It is also capable of generating html reports with the scan results.
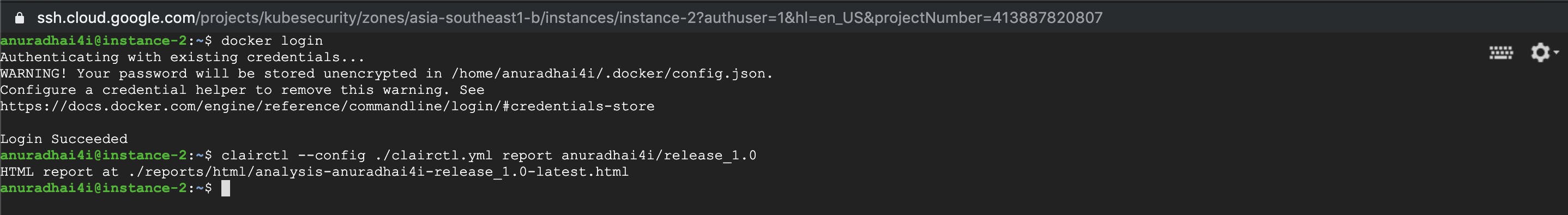
A fraction from the HTML report:
Conclusion
It is an essential practice to incorporate security testing to the CI/CD pipelines in a DevOps environment. In modern software delivery platforms using containerisation, we must also consider a way to scan the container images before shipping them to clients and production environments. Thus, we can use CoreOS Clair and other related tools that provide static scanning for container images.
What’s Next?
In part 2 of this session, I will cover the installation and set up of Clair with different deployment methods while exploring Klar and Clairctl tools. Until next time!

